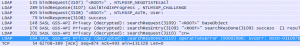
It turns out that LDAP is encrypted using Kerberos. Wireshark can decrypt these frames.
I’m on Windows, so I had to install 32bit Wireshark (64 bit doesn’t have Kerberos decryption). You then need to generate a keytab file. ktpass is installed on windows server 2012 (or it was on mine at least, earlier versions may require the support tools). The following command will create the keytab file (the user I used was the user that was communicating with the LDAP server for the communication I was trying to debug).
ktpass /princ username@FQDNDOMAIN /pass user-password /crypto RC4-HMAC-NT /ptype KRB5_NT_PRINCIPAL /out file.name
You can then open the capture in Wireshark and go to Edit->preferences->Expand protocols on the left->select KRB5. Then select your keytab file, and tick the ‘Try to decrypt Kerberos blobs’ check box. Then all your encrypted frames should be decrypted. If it doesn’t work, there are no error messages, it just doesn’t do anything.
I initially tried creating the keytab using ktutil on centos (from the krb5-workstation package). This didn’t work.